First off, welcome to the Shandy Blog and for taking interest in our writeup of the 3rd Trace Labs Global CTF for Missing Persons! We must apologize for the delay in writing this up too. February is an extremely busy month for all of us and we have been telling several dozen people now that the writeup would be out “soon” haha. For those looking forward to the read we hope that it is worth the wait, and that you can take away even a little piece of information, tip or trick that we used!
The TraceLabs Global Missing CTF III: An OSINT CTF for Missing Persons event took place on February 1st 2020, and Shandyman and the Three Half-Pints entered the event targeting a Top 10 finish. In the end, we finished 2nd out of 184 teams in a fiercely close duel with the previous winners “TheManyHatsClub”!
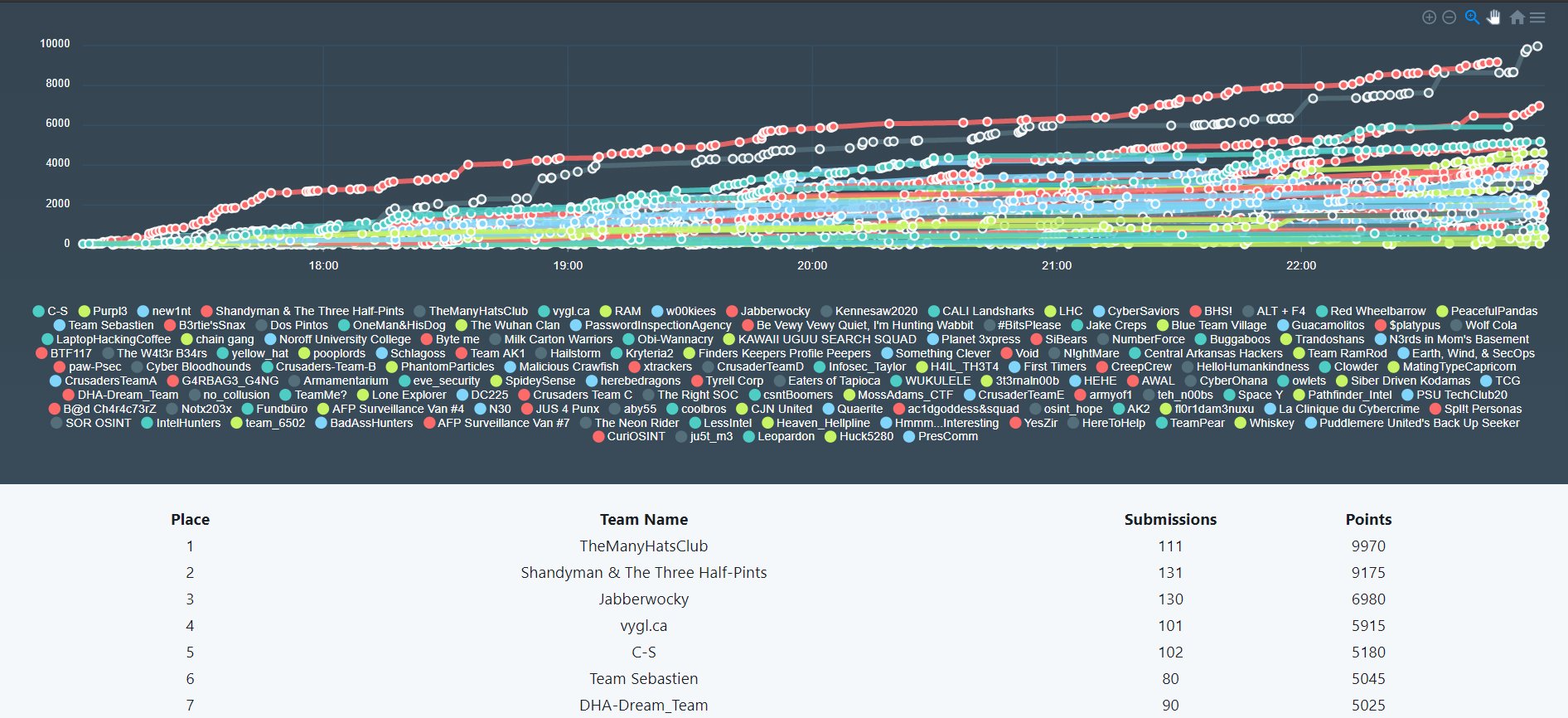
(Above: The Final Scores are tallied at the end of the 6-Hour CTF)
It was a very close race all the way through, and we are looking forward to competing again in future events! Hopefully next time we will have more beer though…Shandyman ran out of beer 4 hours in to the event which definitely cost the team at least 1500 points!
The First Step – Recruiting the Team
After our success in the 2nd Annual Trace Labs Global CTF, we decided that entering the 3rd installation of the event was an absolute must. Originally, we were supposed to run with the same team as before, however one of our Team Members had just become a new Father (Congrats again!), which would see him sidelined for the main event on February 1st, and the team reduce to just “Two Half-Pints”.
The Team consisted of myself and 2 colleagues from work, however only one Half-Pint had experience working in Threat Intelligence/OSINT (Just under a years’ worth!). The rest of the team consisted of 2 Incident Responders. While we all have experience in InfoSec, it’s nothing when you combine the total knowledge and experience in this area.
Finally, we add a sprinkle of Skype, a bit of swearing and a dash of beer in to the mix, and the 3rd “Shandyman and the Three Half-Pints” team was born. We decided to keep the name as it was in the last couple hours leading up to the event, with the main reason for this being cited as “lol why not”.
Recon of the Mind – Avoiding Previous Mistakes
Let’s face it: When you come second and you have a competitive mindset, the first thing you think is “IF YOU AINT FIRST, YOU’RE LAST!” (That’s a quote from my best friend Ricky Bobby). We didn’t want to have a repeat of this, so the week before the CTF began, we decided to dedicate it to working on our flaws. We noticed two major issues from the previous Global CTF that we also placed 2nd in:
The first one was that we went stale for nearly 3 hours with no points. It was decided from there that we would then move on to perform research on other missing people at that time. We would split the missing persons between the three of us, and if nothing was found within a 15-20 minute window that provided any value, then we would rotate those choices to another team member.
I cannot stress enough how valuable this is. When you take part in these events, teamwork is the most important aspect, but also realizing the strengths of each of your teammates will massively help out. After we traded missing persons, the points then started to creep back in again, finding noticeable points of interest where other teammates would have ruled it out. In all honesty, this was probably the difference between finishing 2nd and finishing 15th.
The second point was that we spent far too much time chasing the 1000-point challenges. Don’t get me wrong, finding and cracking a leaked password of a missing person is very easy when you have 2 x Titan X’s, Salts and the Hash, but too much emphasis was put on getting the big results. You really underestimate the amount of points you can get when you are submitting 20, 50 and 150pt pieces of information. Again, like above, this was the difference between a high podium finish and the doldrums.
With those two major points covered, we were armed and ready to compete again. The “meta” of the competition had changed slightly, since passwords were now only seen as 150pt (Advanced Subject Info) classifications, but it didn’t matter to us. At the time…
Tool Revision
Another thing that we vastly underestimated was the use of automated OSINT gathering tools during the event. I’ll be honest, we used a huge number of tools. I think the grand total number of tools was…..0?? Yup, we used no automation when taking part in ANY of our events. Even in this revision (The 3rd Global CTF), very limited tools were used. Things like NameChk and Whitepages are second nature in these investigations, however learning how to use the Open-Source Spiderfoot Python Modules, and adding your own API’s to each script would have massively helped out! That’s a topic for the next CTF!
What’s a DarkWeb?
I should note; this was our
weak point. Usually we have a couple of publicly leaked databases that we can
reference when it comes to discovering email addresses. Being able to grep 20GB
of CSVs for information regarding an email address can be very powerful
information, depending on what is hosted in that Database.
This time however, we came across no email addresses. And when we eventually
found an email, there was no information regarding it. That’s where darkweb
searches could come in to play. Finding any indication of a missing person on
the DarkWeb could prove critical, as more often than not this could indicate
nefarious behavior by the individual, or could even indicate foul play.
Spiderfoot and specific Maltego machines will help you search the most common
Dark Web Search Engines but if you are not familiar with either of these, you
may be at a disadvantage. Still, you can use Tor2Web sites like Ahmia to browse various .Onion Websites. For the
Shandymen though, we need to improve on this.
The Game Plan – Navigating the CTF Minefield
Okay, we’ve done this before. You would think we would at least know where to start? Unfortunately, no. Each Missing Person Case is different, as each missing person might have no presence on the internet. It’s very difficult to know where to navigate.
For the Shandymen we took a simple psychological approach. Most people only really started to use the internet heavily in the mid-2010’s. Of course, this is different from person to person, but most commonly this will be the case. This coincides with the rise of Social Media (We’re talking Facebook and Instagram here). You can use this to whittle down a list of the most likely candidates with Social Media presence. For starters, you can almost instantly rule out chances of uncovering a treasure chest of information on Social Media, for people who have been missing for over 1500-ish days (4-5 years).
With that we got started. Instead of focusing on 8 Missing Cases, we were zoned in to 5 Missing Cases. From here it’s just a matter of saying “I dibs this one” to your teammates! Spend 15-20 minutes researching the Missing Person and decide from there whether or not spending another hour or so could potentially be worth a lot of points. Once you’re satisfied with your findings, get a teammate to run a quick search over your information to ensure you didn’t miss anything. Usually this takes about 10 minutes but it depends on how much you found!
The Shandy Search is a pretty simple workflow to follow: Missing Report -> Reverse Image (Optional but very useful – Use Yandex) -> Facebook (And iterations of the person’s name) -> Mass PIVOT!

Using this we are able to draw points very quickly. Each team member had their own attention to detail and were able to spot things that other teammates would miss. Peer review is an absolutely essential part of OSINT and asking your Teammates for validation of a potential submission could mean the difference between 10th and 1st place. Remember to work together!
Pipped
This is a section that I really was not looking forward to writing, but hey ho we made it so you get to hear it!
Closing out the competition at 4am GMT, Shandyman & The Two-Half Pints were sitting in 1st place almost 1800pts ahead of our nearest competitor. The submissions had stopped and the final submissions were being tallied.
Almost as if we were cursed, TheManyHatsClub managed to uncovered 2 DarkWeb Submissions for 2000pts, in the last 5 minutes of judges scoring after the competition ended. We played well but yet again the Shandymen were destined to finish 2nd to TMHC!
I’ll be honest at 4:20am when we were relegated to 2nd place, I nearly burst in to tears. To be as competitive as Shandyman and be pipped in the last 5 minutes for the win, that one hurt a lot. At the time, OSCP was a mega goal for me personally and for our team, but the best team won in the end and we are gracious in defeat! The main takeaway however is that collectively we had submitted 130+ potential leads for Missing People that would go to local law enforcement, and hopefully help them locate these missing people. That’s a pretty nice feeling, to know you’ve done something good like that for others, while having fun at the same time.
We chatted to TMHC for a while afterwards and eventually joined their Discord channel (Which is pretty good by the way, shameless plug) and started thinking of how we would draft this Writeup! A few of the Shandymen are hoping to meet a couple of the winning TMHC members at a Security Conference to buy them a beer. Or Seven. Or shots. Or Shots in Beer.
Thanks again to TraceLabs for putting together an absolutely fantastic event. We always look forward to these throughout the year, and the feedback is always second to none from all participants! Thanks also to Dean O for access to his ‘Open Source Intelligence – Basic to Advanced‘ Udemy Course, we will definitely put it to good use!
If you enjoyed this writeup or would like to contact our team for any reason, reach out to us! We don’t bite and we’re happy to chat with you!
No responses yet